- 832.753.7557
- info@jurisec.com
Home / Cybersecurity Framework Implementation

Our cybersecurity compliance services and assessments identify vulnerabilities and strengthen enterprises’ defenses. Through cybersecurity framework consultation, we design powerful security strategies customized to legal operations.
We provide incident response planning and endpoint security consulting to ensure quick threat mitigation. Our cybersecurity services safeguard client data, maintain regulatory compliance, and reduce exposure to cyber threats.
Business achieves proactive, resilient, and continuous security readiness.
Our services focus on implementation to protect organizations from evolving cyber threats. We integrate technical, administrative, and procedural safeguards, ensuring resilient systems, regulatory compliance, and continuous protection for sensitive client and business data.
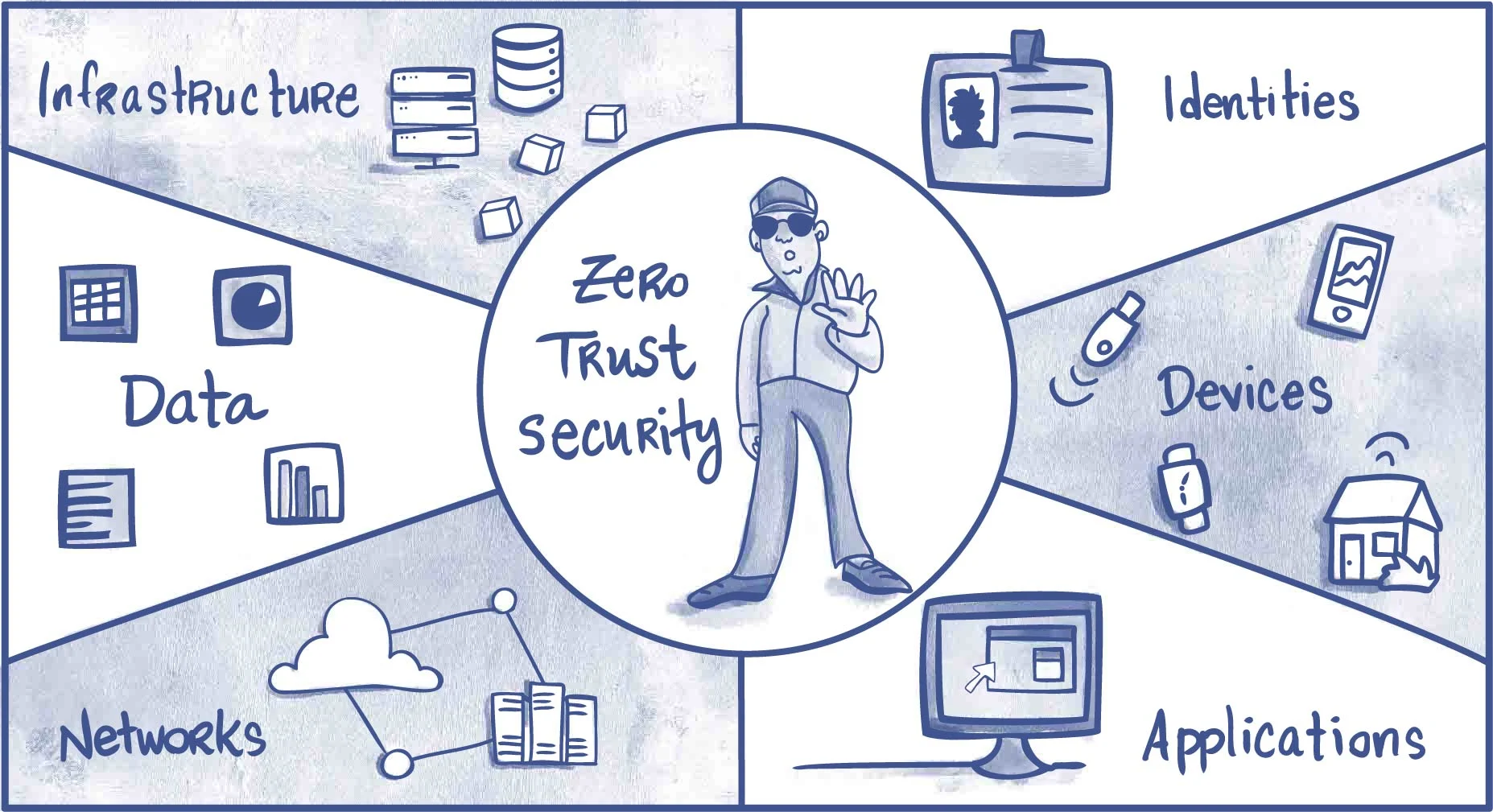
We design and align Zero Trust and defense-in-depth strategies, ensuring layered security, strict access control, and comprehensive protection across all digital assets and communication channels within organizations.

We deploy industry-standard frameworks, including CIS Controls, NIST CSF, and ISO 27002, to enhance cybersecurity posture, enforce best practices, and maintain regulatory compliance efficiently.

We provide personalized training programs that educate staff on cyber risks, secure practices, and regulatory compliance, strengthening human defenses and reducing operational vulnerabilities.
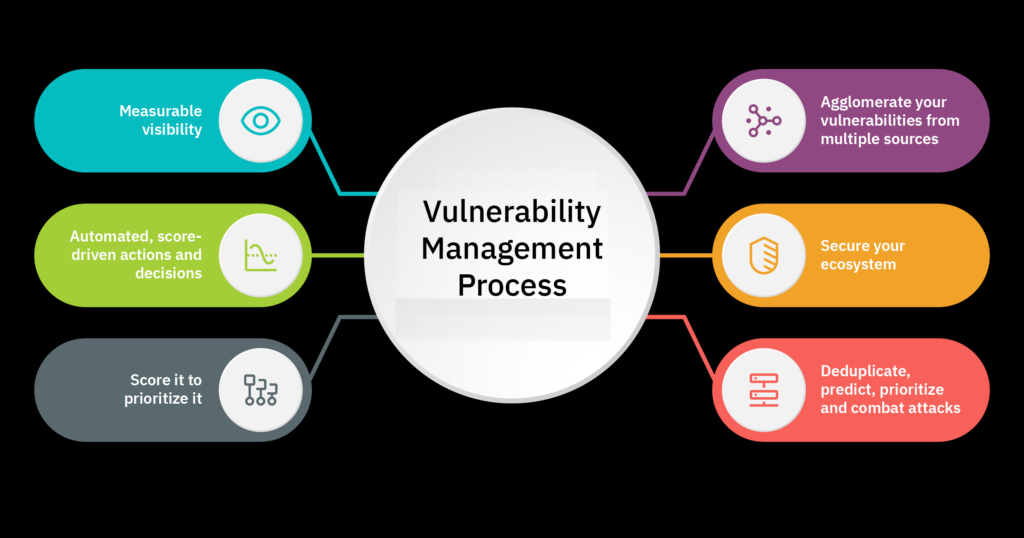
We assess, prioritize, and remediate vulnerabilities using systematic risk scoring, ensuring timely mitigation and continuous improvement of cybersecurity defenses.

We design and implement business continuity and disaster recovery plans to maintain operations, minimize downtime, and protect sensitive data during unexpected disruptions.

We establish structured data governance programs, promoting consistency, privacy, and security across the data lifecycle while ensuring compliance with laws and internal business standards.

We assess vendor risks, monitor third-party compliance, and develop structured oversight programs to protect confidential data, maintain trust, and mitigate exposure to external compliance and security threats.

We develop incident response plans and conduct tabletop exercises to prepare teams for real-world cyber threats, ensuring swift, coordinated, and effective responses.